Providing secure Wi-Fi in a corporate environment often requires separating your internal LAN from guest traffic. This guide explains step-by-step how to set up corporate and guest wireless networks using Ubiquiti UniFi Access Points, an Aruba switch, and a SonicWall firewall. Guest users will have internet access but cannot access the corporate LAN.
This setup includes VLAN configuration, DHCP, firewall rules, UniFi controller configuration, and multicast/broadcast handling to ensure DHCP leases for guest clients work flawlessly.
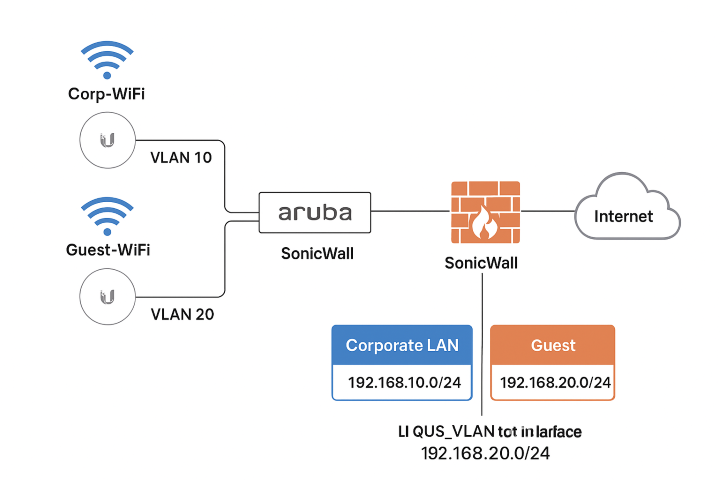
1. Network Design and Plan
Here’s an example network layout:
| Network | VLAN ID | Subnet | Gateway | Notes |
|---|---|---|---|---|
| Corporate LAN | 10 | 192.168.10.0/24 | 192.168.10.1 | AP management on this VLAN |
| Guest | 20 | 192.168.20.0/24 | 192.168.20.1 | Internet-only access |
| UniFi Controller | – | 192.168.10.50 | – | Management IP on LAN VLAN |
Key concepts:
Corporate traffic uses VLAN 10 (native/untagged).
Guest traffic uses VLAN 20 (tagged).
SonicWall handles DHCP, NAT, and firewall isolation.
Aruba switch ports connecting APs and SonicWall are configured as trunks.
2. Configure Aruba Switch VLANs and Ports
Step 1: Create VLANs
vlan 10
name "LAN"
vlan 20
name "GUEST"
Step 2: Configure trunk ports
AP ports: VLAN10 untagged, VLAN20 tagged
SonicWall port: VLAN10 untagged, VLAN20 tagged
Access ports for wired clients: VLAN10 untagged or VLAN20 untagged (guest network if needed)
Example commands for ArubaOS-Provisioning
interface 1/1/24 ! AP port
vlan 10 untagged
vlan 20 tagged
no shutdown
interface 1/1/23 ! SonicWall port
vlan 10 untagged
vlan 20 tagged
no shutdown
If using ArubaOS-CX, the syntax will differ, but the logic remains the same: trunk for APs and firewall, access for end clients.
3. Configure SonicWall Firewall and DHCP
Step 1: Create a Guest Zone
Navigate to Network → Zones → Add Zone
Name:
GuestType: Custom zone
Step 2: Add VLAN sub-interface X0.20
Parent Interface: X0 (LAN)
VLAN Tag: 20
IP: 192.168.20.1/24
Zone: Guest
Step 3: Configure DHCP for Guest
Interface: X0.20
Pool: 192.168.20.10 – 192.168.20.250
Gateway: 192.168.20.1
DNS: 1.1.1.1 / 8.8.8.8 (or internal DNS)
Step 4: Create NAT Policy
Guest network → WAN
Translate source to interface IP
Ensure outgoing internet works
Step 5: Configure Firewall Rules
Deny Guest → LAN
Source: Guest_Net (192.168.20.0/24)
Destination: LAN_Net (192.168.10.0/24)
Service: Any
Action: Deny
Allow Guest → WAN
Source: Guest_Net
Destination: Any
Services: HTTP, HTTPS, DNS, NTP, DHCP
Action: Allow
Optional: Allow Guest → Controller for captive portal
Source: Guest_Net
Destination: Controller IP
Ports: 8080, 8443, 8880, 8843, UDP 3478, UDP 10001
Important: Firewall rules are top-down. Place specific allows (like controller access) before deny Guest→LAN.
4. UniFi Controller Configuration
Step 1: Create Networks
Corporate VLAN10: leave blank or explicitly VLAN10
Guest VLAN20: VLAN only, do not enable DHCP (SonicWall provides DHCP)
Step 2: Create SSIDs
Corporate:
Corp-WiFi, VLAN10Guest:
Guest-WiFi, VLAN20, enable Client Isolation
Step 3: Configure Multicast/Broadcast Control (MBC)
Navigate to Settings → Wi-Fi → Advanced → Multicast/Broadcast Control
Whitelist SonicWall MAC to allow DHCP offers to reach guest clients
Save & apply
This step is crucial. Without whitelisting the SonicWall MAC, guest devices will not receive DHCP leases on VLAN20.
5. Testing and Verification
LAN test: Connect a wired client to VLAN10, verify internet and LAN access.
Guest test: Connect to
Guest-WiFiConfirm IP: 192.168.20.x
Confirm internet access
Confirm cannot reach LAN devices
Confirm guest clients cannot see each other (Client Isolation)
Firewall logs: Monitor blocked and allowed traffic
Optional: packet capture for debugging
6. Best Practices
Use WPA2/WPA3-Enterprise for corporate SSID, WPA2-PSK or captive portal for guests
Enable logging for guest activity
Consider bandwidth limits on guest network via SonicWall or UniFi
Keep all devices updated: UniFi APs, controller, Aruba switch, SonicWall firmware
Document VLAN IDs, IP ranges, and firewall rules
✅ Summary
Create VLANs and trunk ports on Aruba switch
Configure SonicWall: Guest Zone, VLAN sub-interface, DHCP, NAT, firewall rules
Set up UniFi networks and SSIDs, enable client isolation
Add SonicWall MAC to UniFi MBC whitelist to allow DHCP
Test connectivity and firewall isolation
Apply best practices for security and monitoring
This configuration ensures:
Corporate and Guest Wi-Fi are properly segmented
Guests get DHCP addresses and internet access
Guest devices cannot access corporate LAN
APs can efficiently handle broadcast/multicast without blocking DHCP
